As the world gets a more politically complex place, with both overt and covert hostilities increasing between various countries, things appear to be hotting up in the digital security world – or at least being noticed by the powers that be !! Here in the UK the Financial Times is reporting this week that it has seen a letter between the the UK Gov and the likes of Vodafone, O2 and EE advising them they they should be “careful” over which companies they choose as suppliers whilst building their 5G networks (5G rollout is currently a top priority for UK telcos enabling them to support high speed wireless Internet and a massive amount of Internet of Things tech over the coming years). It has been suggest the letter is directed at a handful of Chinese manufacturers, such as Huawei and ZTE, which may be barred from the 5G process altogether over national security concerns, and possibly prompted by shortcomings highlighted in a recent report by UK Gov cyber security evaluation centres working closely with manufacturers evaluating their hardware.
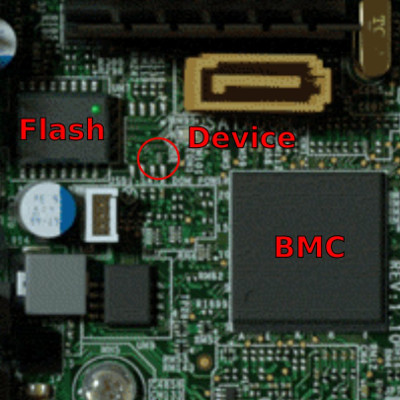
This comes on the back of news last month from Bloomberg that it is alleged for some years devices – “spy chips” as Bloomberg say – have been inserted into hardware developed by San Jose-based Super Micro during it’s overseas manufacture that underpins a variety of cloud services, such as Apple, Amazon and others. It is alleged the devices – just a small black box IC which were made to look like passive run of the mill parts that would not look out of place – were added by an Asian manufacturer without permission. These devices could for example inject malicious code into the core of the Baseband Management Controller (BMC) – management firmware used for remote access even if a machine is off – in order to gain backdoor entry and exploit the servers of large cloud providers.
Whilst the detail here from Bloomberg is unclear, and various counter-claims have been made, it does highlight the difficulties and risks associated where commercially or financially sensitive hardware is manufactured down the end of a very long supply chain, and the challenges involved with the associated control and traceability of components used. It is also easy for tech product developers to sometimes overlook the weak points in a design – for example related to the story above, legitimate concerns have been previously been highlighted by the security community about weaknesses in BMC implementations. Also it can be easy for developers to take their eye off the ball during mass production of PCBs – often which have parts “substituted” by factories to get prices down or solve availability problems. This can lead to design copyright theft in the best case, or large scale manipulation or exploitation by “bad actors” at worse.
As we surround our daily lives with more hardware, such as voice assistants, mobile phones and smart internet of things devices we need to be careful exactly what we are letting take control of our daily lives. Companies selling their products also need to be sure that they are not letting the criminals in the back door by hardening their designs against hostile threats – both hardware and software – and ensuring they have trust in their supply chain.
Here at Milliamp we have significant skill in the secure design of hardware and software systems to resist software and hardware attack by remote and physical threats, including during manufacture in distant factories ! This experience includes secure crypto technology, financial EMV hardware, TPM, firmware encryption and tamper detection technology. We are also able to ensure that our customers designs are securely manufactured and protected against modification or copyright/cloning in untrusted OEM factories. We are also able to undertake security focused design reviews and factory/test rig audits. Get in touch for more info.



Leave a Reply
You must be logged in to post a comment.