A few weeks ago a major cyber attack occurred that knocked offline a large part of the Internet including Facebook, Twitter, Amazon, but more seriously public web services and even government infrastructure in Sweden. This attack did not originate from some Bond villain style lair, but instead from the innocent looking white goods technology products in homes and offices across Europe and the world.
We hear a lot about the Internet of Things (IoT) but unfortunately not a lot about security of the IoT. With our rush to make our everyday lives smarter, many companies and governments are neglecting to focus on what happens when tech around us is weaponised via their Internet connections by online hacking groups or even hostile foreign governments.
These devices can be anything from TVs, smart thermostats, to web-connected doorbells. Once remotely controlled, these devices can then go on to collectively disrupt the Internet, participate in cyber crime activities such as distributed attacks on online banking, and even spy on their owners such as eavesdropping in places they are located even when appearing in standby/off.
Update Mar 2017: It does appear that these sort of vulnerabilities do exist, as confirmed by released “Vault 7” documents from Wikileaks showing that Samsung TVs are vulnerable to attack according to Wired.com – bearing in mind that they can be exploited by anyone with the right know-how – not just governments.
The recent attack on Dyn, Inc. appears to be linked to the Mirai botnet, taking advantage of exploits in technology designed and manufactured by the Chinese tech firm Hangzhou Xiongmai (XM) that is reused in a variety of consumer goods such as on-demand TV DVR’s to web enabled security cameras.
Whilst the manufacturer is not directly at fault, poor design and manufacturing control of white goods “integrators” using XMs modules resulted in many of these devices unknowingly being shipped to end users with a well known default configuration and the same factory password set. This allowed remote control of these devices by 3rd parties, creating a massive global botnet that was able to flood Dyn’s services, or anyone else’s for that matter, with masses of data, overloading them and taking them offline.
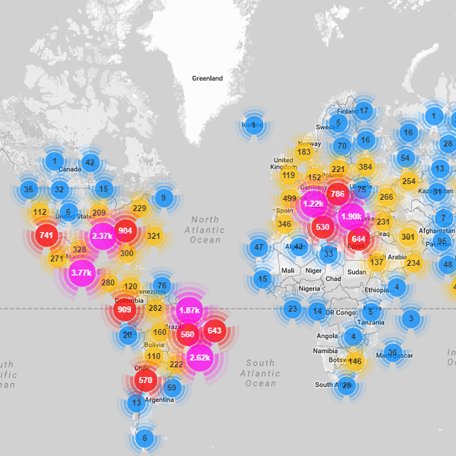
In this instance only around 100,000 malicious endpoint “zombie” devices were utilised in the distributed denial of service (DDoS) attack, but this was enough to generate a massive data storm of well over 1.2 terabits per second (1.2Tbps), the largest attack of its kind in history, and these types of attacks continue to increase every day across the world.
Anonymous have claimed responsibility for the Dyn attack, and the post mortem of events shows this was a simple unsophisticated “script kiddie” exploit. It is very concerning to think what could have been if a more adept, organised or well funded hostile organisation carried out an attack like this. And don’t forget, Mirai is still out there, could it even be on your wall right now inside your thermostat !?
Milliamp Technologies have decades of experience of hardware, embedded firmware and software development, with particular experience in embedded design security, embedded information security (InfoSec) including encryption, communications security and active Internet/cloud monitoring with intrusion detection. We are able to ensure our customer’s designs are robust and actively protect their users against threats exposed to them direct attack such as reverse engineering or by connection to public networks such as the Internet.
If you have a design that needs it’s security beefing up – either with software or strong hardware protection, or just a bit of advice – please get in touch !


Leave a Reply
You must be logged in to post a comment.